SEC Twitter Account Compromised by SIM-Swapping Attack
This week, the US Securities and Exchange Commission confirmed that its X (formerly Twitter) account was hacked after a SIM-swapping attack on the cell phone number connected to the account. Earlier this month, the SEC’s X account posted a message claiming that ‘Crypto ETF finally approved by US regulator’ – of course, that was a false news posted by a hacker.
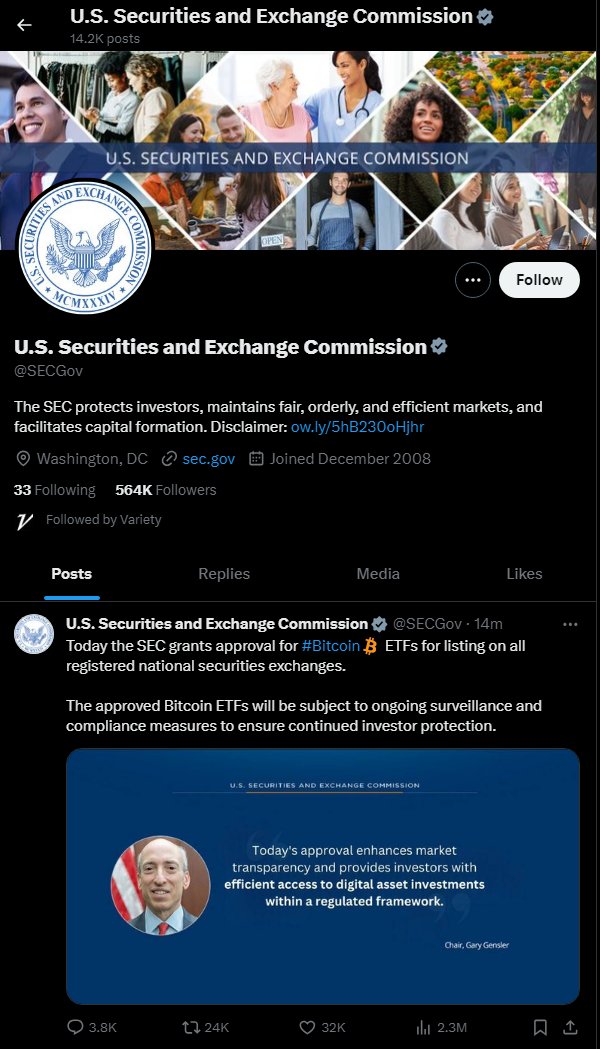
The @SECGov X account was compromised, and an unauthorized post was posted. The SEC has not approved the listing and trading of spot bitcoin exchange-traded products.
— U.S. Securities and Exchange Commission (@SECGov) January 9, 2024
According to the SEC, in their investigation they found that the cell phone account associated with the @SECGov Twitter account was subject to a SIM-swapping attack. And that was what led to the compromise of the SEC’s account: ‘The unauthorised party obtained control of the SEC cell phone number associated with the account in an apparent “SIM swap” attack,’ as the SEC press statement put it. And apparently multi-factor authentication (MFA) had been previously enabled on the @SECGov X account, but then it had also been switched off by X Support.
What is a SIM-Swapping Attack?
This is a common variety of identity theft dubbed SIM-swapping. In this attack, the hacker forces a mobile phone provider to transfer a victim’s mobile phone line to the attacker’s mobile phone. Such ‘SIM-jacking’ is possible with mobile telephone networks such as the T-Mobile, ATT, Verizon, Celcom, Telus, Rogers and H3G platform. Essentially, this attack leverages a mobile telephone carrier being tricked into executing a ‘port-in’ and ‘port-out’ (porting in a customer to a device under the attacker’s control and porting out a customer from a device under the attacker’s control). If successful, this simple expedient grants hackers the ability to intercept texts or phone calls on the device – including password reset links and the one-time passcodes required for any MFA.
Sim Swapping attacks are popular techniques these days, when fraudsters seek to access other victims’ accounts, ranging from social media platforms to email services and even bank accounts. It is achieved by pilfering a victim’s phone number so recovery messages for the other accounts can be intercepted, which can then be used to bypass the safeguard of two-factor authentication.
There are several methods through which an attacker can carry out SIM-swapping:
- Phishing: The attacker deploys a phishing attack and the user instead clicks on this link and either send the attacker their personal information (such as mobile number and bank details) or the two eventually become friends on a social medium such as Facebook.
- Social Engineering: The attacker masquerades as the victim and calls the mobile phone provider with the victim’s information and ask for victim’s number to be transferred to his mobile phone number.
- Hacking: The attacker gains access to the victim’s account through phishing (sometimes using stolen credentials) or directly enters the victim’s mobile carrier’s system using stolen credentials.
As soon as the spoofed SIM card is put into effect, the attacker begins receiving messages intended for the victim, among them two-factor authentication codes, banking text messages, and anything else that would be sent to the victim’s phone number by legitimate services. This provides a portal through which the attacker can get into other accounts associated with the victim’s phone number.
SIM-swapping can have severe consequences for both individuals and organizations:
- Monetary loss: The victim can be exposed to losing any amount of money, ranging from a little amount to all of it This can happen, for example, when the attacker gets their hands on banking details or cryptocurrency wallets.
- Identity theft: By gaining access to the victim’s phone number, an attacker also gains access to accounts attached to that phone number, including social media and email accounts the user has associated with their mobile number. This can lead to identity theft and fraud on the victim’s behalf.
- Cyber Attacks: SIM swapping can be a technique used to infiltrate other web-based accounts, like profiles on social networks or e-commerce stores that might serve as first steps to attacks or a means of spreading disinformation.
In this case, the SEC’s credentials were stolen by attackers who hacked into the administrative controls of the mobile phone carrier and used the sim-swapping attack. The SEC’s confirmation demonstrates that MFA systems using SMS-based OTP are vulnerable to SIM-swapping attacks. If you have only two arms to authenticate yourself, the hackers might just authentication is clearly not foolproof. If they use SMS as the delivery mechanism for these OTPs, then they are still vulnerable to attacks on the SIM card. The X account hack of the SEC must be seen as a wake-up call for organisations – both private and public – as well as individuals and service providers to take the threat posed by SIM-swapping attacks seriously. They must also make it a priority to strengthen their security controls and adopt a comprehensive and sustainable counter-swapping strategy to safeguard against the newest and most pervasive digital tomorrow.
For more cybersecurity news and updates, follow us on Cybersecurity – The SOC Labs.
Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The SOC Labs assumes no liability for the accuracy or consequences of using this information.
